Cybersecurity is an extensive topic covering all processes and technologies that keep systems and important data secure. In today’s world, where almost all our activities are increasingly connected to the digital environment, it is obvious that the importance of cybersecurity is on the front burner. Apart from more and more data being transferred within the online environment, the spectrum of cyber threats broadens and its sophistication increases. All affected entities should therefore adapt to this fact by implementing efficient defence and security strategies. For this purpose, there are cybersecurity frameworks aimed at helping organisations protect their digital assets and sensitive data.
Cybersecurity and cybersecurity frameworks
Cyber-attacks and threats are on the rise and their significant impact means that organisations must find an efficient and reliable solution – as soon as possible. Effective data protection and robust measures designed to prevent or minimise risks related to the digital environment are not a matter of course. These measures are closely connected to the draft and implementation of a resilient cybersecurity strategy, which should comprise various components, such as firewalls, antivirus software, encryption, security policies and training or data backups.
Cybersecurity frameworks are designed to help organisations reach this ideal state. That is, they are an important instrument for strengthening cybersecurity comprising methods, directives and best practices that enable organisations to plan, evaluate, adjust, implement and manage their measures aimed at enhancing cybersecurity and information security.
From CSF 1.1 to CSF 2.0
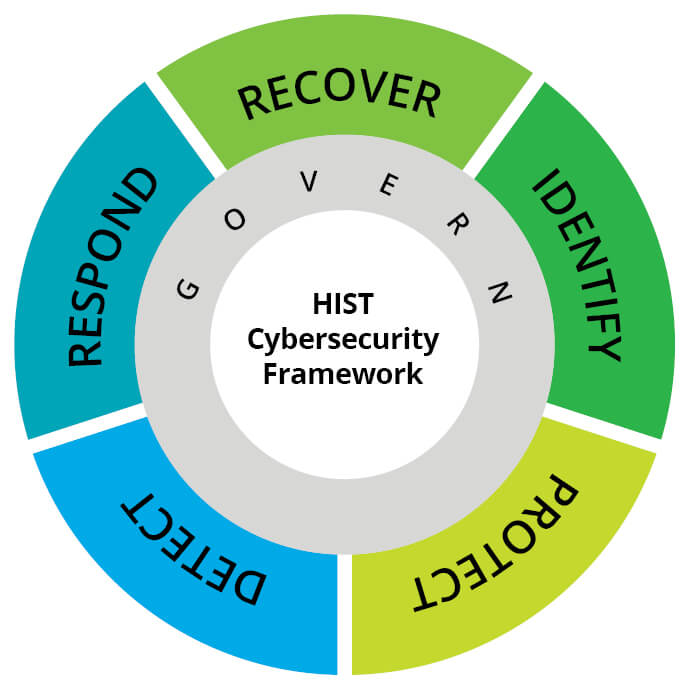
There are several different frameworks, each with specific characteristics and focus. One of them is the Cybersecurity Framework (CSF) developed by the National Institute of Standards and Technology (NIST) in the United States, which has become one of the leading “guides” in the field of cybersecurity. This framework offers organisations a structured yet flexible approach to building and improving their cybersecurity. It focuses on five main fields or functions:
In the dynamic environment in which organisations operate nowadays, such approaches must keep evolving to prevent rigidity in organisations that use them. Thus, after almost ten years since the release of version 1.1, NIST CSF underwent a thorough revision responding to the dynamic changes in technologies, risks and the overall cybersecurity landscape. The updated version of the framework called CSF 2.0 was expected to come at the beginning of 2024, arriving at last by the end of February.
Following the preceding versions, CSF 2.0 introduces new functions emphasising the importance of administration and supply chains. Special attention is given to Quick Start Guides to ensure that the framework is relevant and easily available to both smaller organisations and their bigger counterparts as long as possible. Thus, the main changes reflected current and future challenges in the field of cybersecurity and consisted in making the framework more user-friendly for all organisations.
Moreover, NIST added a sixth field to version 2.0 (“Govern”) that focuses on the processes by which organisations adopt and implement decisions related to cybersecurity. This new field runs through the five original fields and emphasizes the human factor, processes and technologies necessary for efficient cybersecurity management. This is also why, in the newest visualisation, this field is pictured in the middle – as it impacts the way the organisation will implement the other five functions. Thus, with one brand new field, some categories had to adapt to a new arrangement; therefore, we will find some of them exclusively in the “Govern” field, including supply chain risk management and risk management itself, which, in the preceding framework version, were part of the “Identify” field.
Other significant changes in the CSF also include the CSF 2.0 Reference Tool, which simplifies implementation and enables users to search and export basic guidance data in user-friendly and machine-readable formats. Additionally, a searchable catalogue enables companies to compare their activities with the CSF and to connect them with more than 50 other documents on cybersecurity, which makes complex risk management easier.
CSF 2.0 represents a significant advancement from the original framework with updates designed to handle current and future challenges in the field of cybersecurity. However, it remains a voluntary framework, which includes not only its specifics, but also references to the first and second Network and Information Systems Directives (NIS and NIS2) and the ISO 27000 standard (set of standards for information security management), which form an important part of the whole cybersecurity ecosystem. Thus, CSF may be a useful tool for organisations aiming at compliance with the NIS2 requirements and meeting the ISO standards focused on specific information security management processes. By combining these three aspects, CSF 2.0 enables organisations to achieve a higher security level and to meet several regulatory requirements.
Why is the assessment of a cybersecurity framework important?
Cybersecurity framework assessment is a key step for those striving to ensure the effective protection of information systems and data – it is a way to identify and solve security risks and, as a consequence, to better allocate funds to reach the optimum state of security.
By regularly assessing the cybersecurity framework, you may identify and better prioritise reactions to potential threats, and identify gaps in meeting specific standards, thus ensuring a timely correction; this is also related to an overall identification of weak spots not only regarding security measures aimed at known threats, but also concerning the necessary adaptation to and readiness for future threats. A strong cybersecurity framework fosters a culture of continuous improvement and adaptation, and it helps protect reputation and sensitive data with which a lot of entities work every day. This is also why continuous improvement is crucial.
This requires, among other things, identifying important cyber-capabilities that should be invested in, particularly given the specificity of the business field and threat analysis. At Deloitte, we therefore focus on the capability analysis of each entity as well as their business field and relevant threats.
We believe that, even though security itself is vital, it is also important to stay alert and build resistance concerning the evolving threat environment. We find it useful to reflect these aspects in the long-term strategy but also in the management model in the direction in which the entity will advance in terms of cybersecurity. The objective is not only to introduce necessary structures and rules for the maintenance and improvement of own cybersecurity capabilities reactively, but also to introduce proactive protection against cyber-attacks. This also comprises overall resistance, referring to the ability to respond to cyberattacks efficiently and recover from them as soon as possible, but also vigilance, including the ability to detect internal and external threats by collecting information on threats, and thus preparing for them proactively.